Research Interests
My research interests are focused on computer networks, in particular the areas of security and privacy of wireless networks. I am involved in identification, modeling and mitigation of security vulnerabilities in network systems, design of secure wireless communication protocols, and performance analysis for wireless network systems. My current projects are in location privacy in wireless sensor networks (WSNs) and denial-of-service attacks in wireless networks.
Hiding Contextual Information in Wireless Sensor Networks
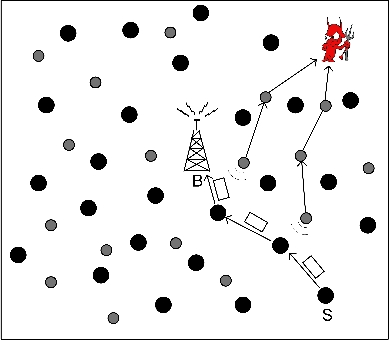
Figure 1: Co-existance of a WSN with an adversarial network.
Recent advances in sensor technology have led to the manufacturing of cheap, compact, battery-operated devices outfitted with wireless transceivers. Such devices can be self-organized to a wireless sensor network (WSN) that can effectively monitor physical parameters of interest at low cost. WSNs find numerous applications in the commercial and tactical domain, including habitat monitoring, target tracking, space surveillance, and others. When collected information is of sensitive nature, its confidentiality is typically secured via cryptographic methods, such as data encryption. However, encrypting the payload of the transmitted data does not protect contextual information such as the location and time of occurrence of a sensed event. For example, in Figure 1, it is shown the co-existence of a WSN with an adversarial network of eavesdroppers. Interception of transmission activity can reveal the occurrence of an event in the vicinity of the source S, the time that this event occurred and the route to the base station. Note that this information is inferred without examining the contents of the communication.
We address the problem of preserving the confidentiality of contextual information under an omnipresent adversary in a resource-efficient manner. We are currently working on a resource-efficient privacy preserving scheme which hides WSN data from a global adversary using fake data sources. This scheme differs from previous solutions in that it employs only a subset of sensors for transmitting bogus traffic.
Selective Jamming Attacks
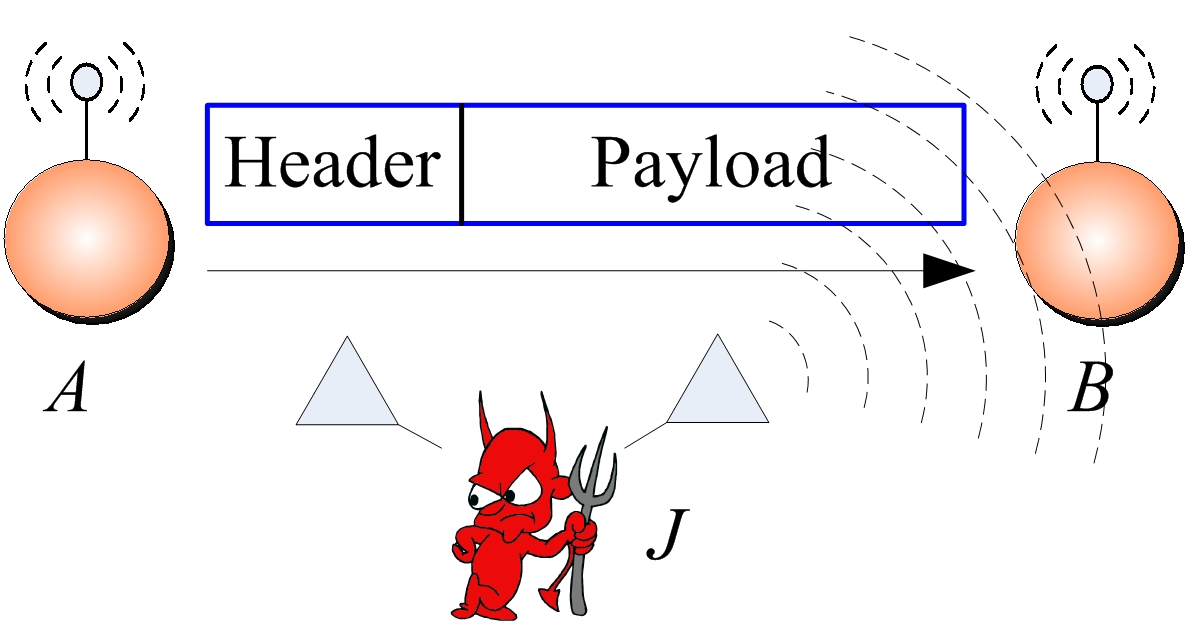
Figure 2: Realization of a selective jamming attack.
Wireless communications are widely employed in different type of network technologies ranging from wireless local area networks to mesh, sensor, cellular, vehicular, congnitive radio and mobile ad-hoc networks. The open nature of the wireless medium exposes the network to security threats such as eavesdropping and jamming. Adversaries can eavesdrop on ongoing communications, inject spurious messages to a legitimate data stream, modify transmitted messages and jam legitimate ones. While eavesdropping, message injection and modification can be prevented by the application of standard cryptographic techniques such as encryption, jamming attacks are much harder to counter. In the simplest form of jamming, the adversary interferes with the reception of messages by transmitting a continuous jamming signal, or several short jamming pulses. However, a more sophisticated adversary can implement a selective jamming attack, in which messages of high importance are targeted. To launch such attacks, the adversary must be capable of implementing a “classify-then-jam” strategy before the completion of a wireless transmission. For example, consider the scenario depicted in Figure 2. Nodes A and B communicate via a wireless link. Within the communication range of both A and B there is a jamming node J. When A transmits a packet m to B, node J classifies m by receiving only the first few bytes of m. J then corrupts m beyond recovery by interfering with its reception at B.
We investigate the feasibility of real-time packet classification for launching selective jamming attacks. We show that such attacks are relatively easy to actualize by exploiting knowledge of network protocols and cryptographic primitives extracted from compromised nodes. Our findings indicate that selective jamming attacks lead to a DoS with very low effort on behalf of the jammer. To mitigate such attacks, we develop schemes that prevent classification of transmitted packets in real time. Our schemes rely on the joint consideration of cryptographic mechanisms with PHY-layer attributes. ![]()
![]()
![]()